API Security Best Practices: A Comprehensive Guide
Introduction to APIs
What is an API?
An API (Application Programming Interface) is a set of protocols that enables different software applications to communicate seamlessly. It acts as a bridge, allowing data exchange between systems, much like a waiter in a restaurant relays orders between customers and the kitchen.
Why is API Security Important?
APIs are the backbone of modern applications, facilitating interactions between web services, mobile apps, and cloud platforms. However, poor API security can lead to data breaches, unauthorized access, and service disruptions. Implementing robust API security measures is crucial to protect sensitive data and maintain system integrity.
Common API Security Threats
Real-World Examples of API Vulnerabilities
- Facebook API Breach (2018): Hackers exploited a vulnerability in Facebook’s API, compromising 50 million user accounts.
- T-Mobile API Breach (2023): Attackers accessed an unsecured API, exposing the personal data of 37 million customers.
API Security Best Practices
1. Authentication and Authorization
- Authentication ensures the API validates the identity of the requesting user or system (e.g., OAuth 2.0, API keys, JWT tokens).
- Authorization verifies whether the authenticated entity has permission to access specific resources.
- Example: A banking app utilizes OAuth 2.0 to securely authenticate users and grant access to financial data.
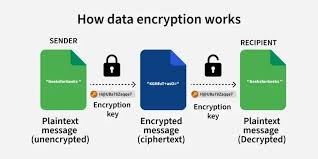
2. Data Encryption
- Encrypt data in transit using HTTPS with TLS (Transport Layer Security).
- Secure stored data with strong encryption algorithms like AES-256.
- Example: An e-commerce site encrypts customer credit card information before storing it in the database.
3. Rate Limiting and Throttling
- Implement rate limiting to prevent excessive API requests and mitigate DDoS (Distributed Denial-of-Service) attacks.
- Example: A weather API restricts users to 100 requests per hour to prevent server overload.
4. Input Validation
- Sanitize and validate all incoming API requests to prevent SQL injection, cross-site scripting (XSS), and other attacks.
- Example: A login system blocks special characters in the username field to prevent SQL injection.
5. Regular Security Audits
- Conduct frequent penetration testing to identify and fix API vulnerabilities.
- Example: A fintech company hires security professionals to conduct quarterly security audits.

2. Data Encryption
- Encrypt data in transit using HTTPS with TLS (Transport Layer Security).
- Secure stored data with strong encryption algorithms like AES-256.
- Example: An e-commerce site encrypts customer credit card information before storing it in the database.
3. Rate Limiting and Throttling
- Implement rate limiting to prevent excessive API requests and mitigate DDoS (Distributed Denial-of-Service) attacks.
- Example: A weather API restricts users to 100 requests per hour to prevent server overload.
4. Input Validation
- Sanitize and validate all incoming API requests to prevent SQL injection, cross-site scripting (XSS), and other attacks.
- Example: A login system blocks special characters in the username field to prevent SQL injection.

5. Regular Security Audits
- Conduct frequent penetration testing to identify and fix API vulnerabilities.
- Example: A fintech company hires security professionals to conduct quarterly security audits.

Visual Representation of API Security
Diagrams and Infographics
Incorporate security architecture diagrams, flowcharts, and infographics to illustrate API security best practices, such as authentication workflows and encryption methods.
Real-World Scenarios
Case Study 1: Twitter API Breach (2021)
Issue: Hackers exploited an API flaw, gaining access to private messages of high-profile users.
Solution: Twitter enforced stricter authentication mechanisms and implemented API rate limiting.
Case Study 2: Equifax Data Breach (2017)
Issue: Attackers exploited an unpatched API vulnerability, exposing sensitive data of 147 million individuals.
Solution: Equifax now conducts regular security audits and applies patches promptly.
Conclusion
Key Takeaways
- Implement strong authentication and authorization mechanisms.
- Encrypt data both in transit and at rest.
- Apply rate limiting and throttling to mitigate abuse.
- Validate and sanitize all incoming data.
- Conduct regular security audits to stay ahead of evolving threats.
Accelerate your Path to a Product based Career
Boost your career or get hired at top product-based companies by joining our expertly crafted courses. Gain practical skills and real-world knowledge to help you succeed.
Reach Out Now
If you have any queries, please fill out this form. We will surely reach out to you.
Contact Email
Reach us at the following email address.
arun@getsdeready.com
Phone Number
You can reach us by phone as well.
+91-97737 28034
Our Location
Rohini, Sector-3, Delhi-110085