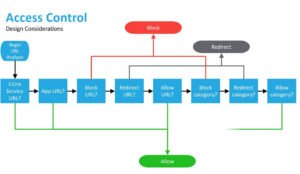
Access Control
Access control is a foundational concept in system security that defines how resources within a computer system are protected from unauthorized use. It involves the mechanisms and policies that govern who can access what, under what circumstances, and to what extent. In operating systems, access control ensures that only authenticated and authorized users or programs can read, write, or execute certain data or operations.
Understanding access control is critical for maintaining confidentiality, integrity, and availability of system resources.
What Is Access Control?
At its core, access control is a method of regulating interactions between subjects (users or processes) and objects (files, memory, devices, applications). The goal is to ensure that only permitted actions are performed on system resources.
This regulation is enforced through a set of rules defined by the system administrator or security policy, using formal mechanisms built into the OS.
Core Components of Access Control
- Authentication: Before access can be granted, the system must verify the identity of the user or process (e.g., through passwords, biometrics, tokens).
- Authorization: Once authenticated, the system checks what resources the subject is allowed to access and what actions are permitted.
- Access Rights: These define the type of operations allowed, such as:
-
-
Read: View content
-
Write: Modify content
-
Execute: Run a file or program
-
Delete: Remove content
-
Permission Change: Modify access control settings
-
Access Control Models
There are several formal models used to implement access control in systems:
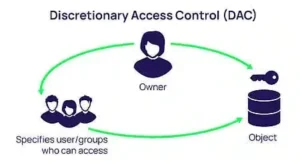
Discretionary Access Control (DAC)
In DAC, access is based on the identity of users and groups. Resource owners (like file creators) control who else can access their resources. This model is flexible but prone to accidental or malicious permission sharing.
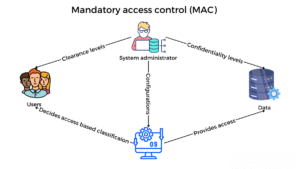
Mandatory Access Control (MAC)
In MAC, access is governed by a central authority and enforced according to security labels (e.g., classified, top secret). Users cannot override these rules. It’s used in highly secure environments like military or government systems.
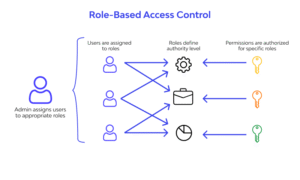
Role-Based Access Control (RBAC)
RBAC assigns permissions based on roles rather than individuals. For example, a “manager” role might have broader access than an “employee.” This model is scalable and often used in enterprise systems.
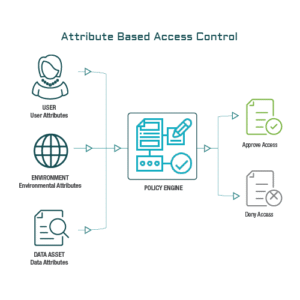
Attribute-Based Access Control (ABAC)
ABAC evaluates access based on attributes (user department, time of access, location, etc.). It’s highly dynamic and suitable for complex, modern cloud-based environments.
Access Control Lists (ACLs) and Capabilities
- ACLs: Each object has a list specifying which users/groups can perform what actions. Common in file systems (e.g., Windows NTFS).
- Capabilities: Each subject (user/process) carries a list of objects it can access and the allowed operations. This model is less common but offers strong isolation.
Importance of Access Control
- Security: Prevents unauthorized data breaches and system misuse.
- Compliance: Ensures that systems meet legal and regulatory standards.
- Integrity: Helps prevent accidental or malicious changes to sensitive data.
- Accountability: Tracks user actions for audit purposes and traceability.