Malware and Threats
In the digital world, security threats are constantly evolving. One of the most significant challenges faced by modern computer systems is the presence of malware—malicious software—and the broader category of cyber threats that seek to compromise data, disrupt operations, or gain unauthorized access. Understanding the types of malware and common threats is crucial for building secure systems and protecting users.
What is Malware?
Malware (short for malicious software) refers to any software intentionally designed to damage, disrupt, or gain unauthorized access to a computer system, network, or data. It operates secretly and often without the knowledge of the user.
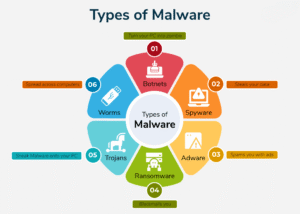
Common Types of Malware:
Viruses
Programs that attach themselves to files and replicate when the file is executed. They can corrupt or delete data and spread to other systems.
Worms
Standalone malware that replicates itself to spread across networks without user intervention. Worms can cause widespread network disruption.
Trojans
Disguised as legitimate software, Trojans trick users into installing them. Once inside, they can steal data, install backdoors, or spy on the system.
Ransomware
Encrypts user data and demands payment for decryption. It’s one of the most financially damaging forms of malware today.
Spyware
Secretly monitors user activities, often stealing sensitive information like passwords, credit card numbers, or browsing habits.
Adware
Floods systems with unwanted advertisements and may track user behavior without consent.
Rootkits
Designed to gain deep-level system access while hiding their presence. They are often used to maintain long-term control over compromised systems.
What are Threats?
A threat is any potential danger that can exploit a vulnerability to cause harm to a system, network, or user. Threats don’t always involve malware—they can also include actions by malicious individuals or accidental errors.
Types of Security Threats:
Phishing Attacks
Deceptive emails or messages that trick users into revealing personal information or downloading malicious content.
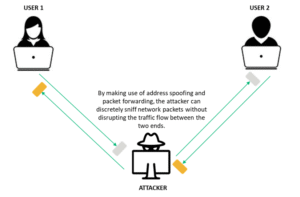
Man-in-the-Middle (MitM) Attacks
Attackers intercept communication between two parties to steal or alter data.
Denial-of-Service (DoS) Attacks
Flood a system or network with traffic to make it unavailable to legitimate users.
Zero-Day Exploits
Attacks that exploit vulnerabilities not yet known to the software vendor or public. These are extremely dangerous and difficult to defend against.
Insider Threats
Security risks that originate from within the organization, often involving current or former employees misusing access.
Password Attacks
Include brute-force, dictionary, or credential stuffing attacks aimed at breaking into user accounts.
The Relationship Between Malware and Threats
Malware is often used as a tool to carry out a broader cyber threat. For example:
- A phishing email (threat) might trick a user into downloading ransomware (malware).
- A Trojan may be used as part of a larger data breach campaign.
Understanding both concepts helps in designing layered defenses that can detect, prevent, and respond to attacks effectively.