DDoS Protection and Rate Limiting: Essential Cybersecurity Strategies
Introduction to High-Level System Design
System Design Fundamentals
- Functional vs. Non-Functional Requirements
- Scalability, Availability, and Reliability
- Latency and Throughput Considerations
- Load Balancing Strategies
Architectural Patterns
- Monolithic vs. Microservices Architecture
- Layered Architecture
- Event-Driven Architecture
- Serverless Architecture
- Model-View-Controller (MVC) Pattern
- CQRS (Command Query Responsibility Segregation)
Scaling Strategies
- Vertical Scaling vs. Horizontal Scaling
- Sharding and Partitioning
- Data Replication and Consistency Models
- Load Balancing Strategies
- CDN and Edge Computing
Database Design in HLD
- SQL vs. NoSQL Databases
- CAP Theorem and its Impact on System Design
- Database Indexing and Query Optimization
- Database Sharding and Partitioning
- Replication Strategies
API Design and Communication
Caching Strategies
- Types of Caching
- Cache Invalidation Strategies
- Redis vs. Memcached
- Cache-Aside, Write-Through, and Write-Behind Strategies
Message Queues and Event-Driven Systems
- Kafka vs. RabbitMQ vs. SQS
- Pub-Sub vs. Point-to-Point Messaging
- Handling Asynchronous Workloads
- Eventual Consistency in Distributed Systems
Security in System Design
Observability and Monitoring
- Logging Strategies (ELK Stack, Prometheus, Grafana)
- API Security Best Practices
- Secure Data Storage and Access Control
- DDoS Protection and Rate Limiting
Real-World System Design Case Studies
- Distributed locking (Locking and its Types)
- Memory leaks and Out of memory issues
- HLD of YouTube
- HLD of WhatsApp
Introduction
What is a DDoS Attack?
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, website, or network by overwhelming it with a flood of internet traffic. These attacks leverage multiple compromised devices, forming a botnet, to generate excessive requests, rendering the target inaccessible to legitimate users.
What is Rate Limiting?
Rate limiting is a cybersecurity measure used to control the number of requests a user or system can send to a server within a specific time frame. This technique helps prevent API abuse, brute force attacks, and excessive server load, ensuring optimal performance and security.
Why Are These Measures Important?
- DDoS Protection: Maintains website uptime and availability by mitigating high-traffic attacks.
- Rate Limiting: Prevents system abuse, enhances security, and ensures fair usage of server resources.
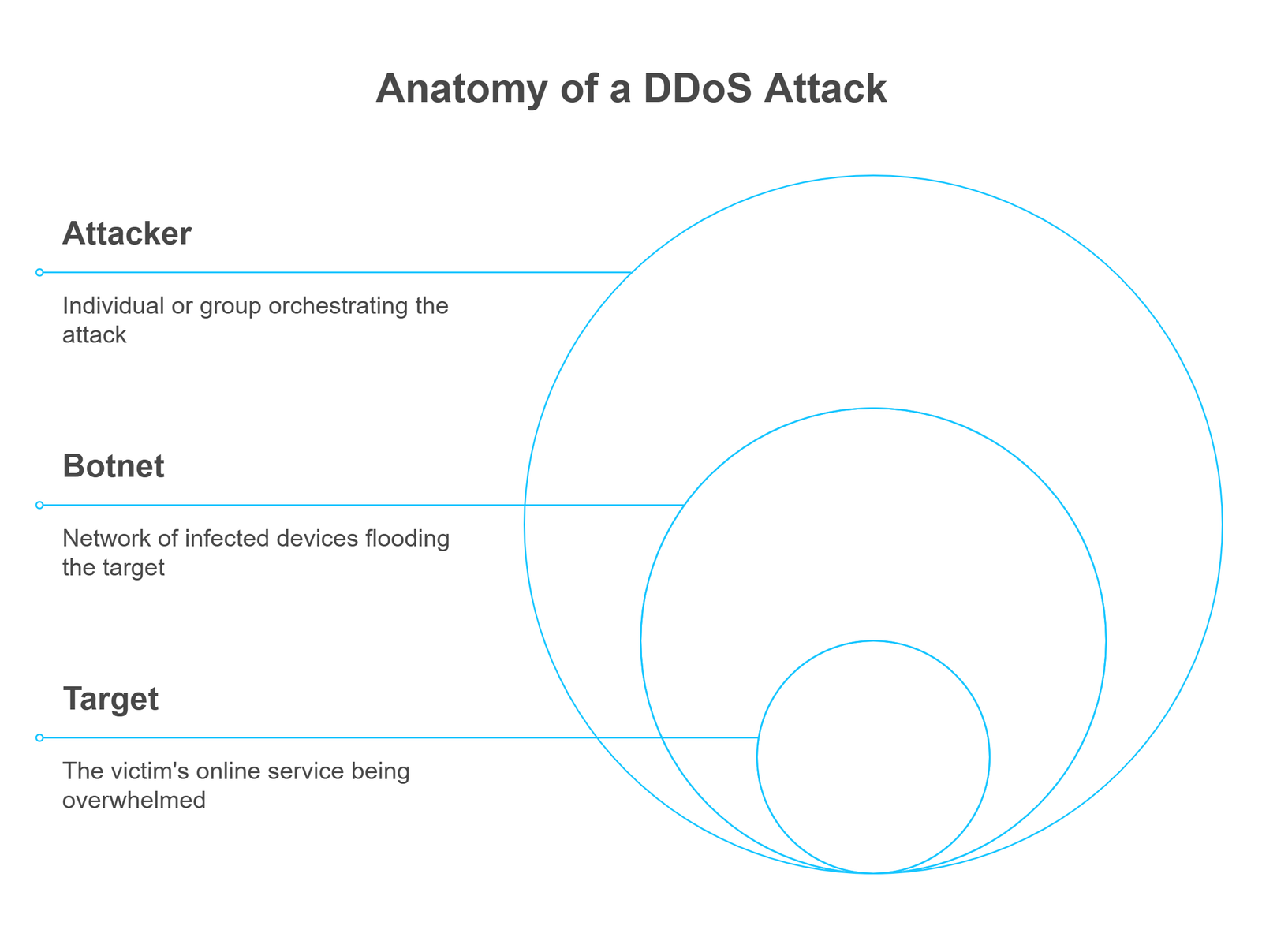
Anatomy of a DDoS Attack
A typical DDoS attack consists of three key components:
- Attacker: The individual or group orchestrating the attack.
- Botnet: A network of infected devices (bots) used to flood the target.
- Target: The victim’s website, server, or online service being overwhelmed.
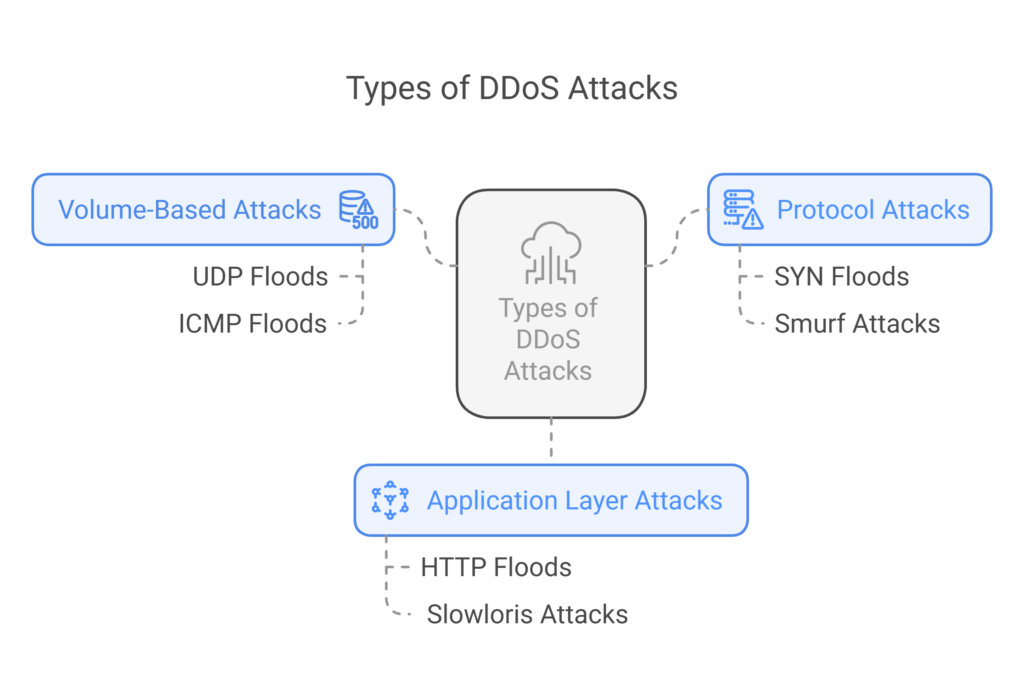
Types of DDoS Attacks
- Volume-Based Attacks: Overload the target with a high volume of traffic (e.g., UDP floods, ICMP floods).
- Protocol Attacks: Exploit network protocol vulnerabilities (e.g., SYN floods, Smurf attacks).
- Application Layer Attacks: Target web applications and APIs (e.g., HTTP floods, Slowloris attacks).
Real-World Example: The 2016 Dyn Attack
In 2016, a massive DDoS attack on Dyn, a major DNS provider, caused widespread outages for major websites, including Twitter, Netflix, and Reddit. This attack was executed using the Mirai botnet, which hijacked IoT devices to flood Dyn’s servers.
In 2016, a massive DDoS attack on Dyn, a major DNS provider, caused widespread outages for major websites, including Twitter, Netflix, and Reddit. This attack was executed using the Mirai botnet, which hijacked IoT devices to flood Dyn’s servers.
Effective DDoS Protection Mechanisms
Traffic Filtering
Traffic filtering detects and blocks malicious requests before they reach the target server. This method helps distinguish legitimate traffic from harmful sources.
Content Delivery Networks (CDNs)
CDNs distribute network traffic across multiple geographically dispersed servers, reducing the impact of DDoS attacks by balancing the load and mitigating excessive requests.
Web Application Firewalls (WAFs)
A Web Application Firewall (WAF) protects web applications by monitoring, filtering, and blocking malicious HTTP traffic, reducing the risk of application-layer attacks.
Real-World Example: Cloudflare’s DDoS Mitigation
Cloudflare, a leading CDN and security provider, uses a global network of servers to absorb and neutralize DDoS attacks, ensuring uninterrupted service for websites and applications.
Understanding Rate Limiting
What is Rate Limiting?
Rate limiting is a technique used to restrict the number of requests a user or IP address can make to a server within a specified time period, preventing server overload and security threats.
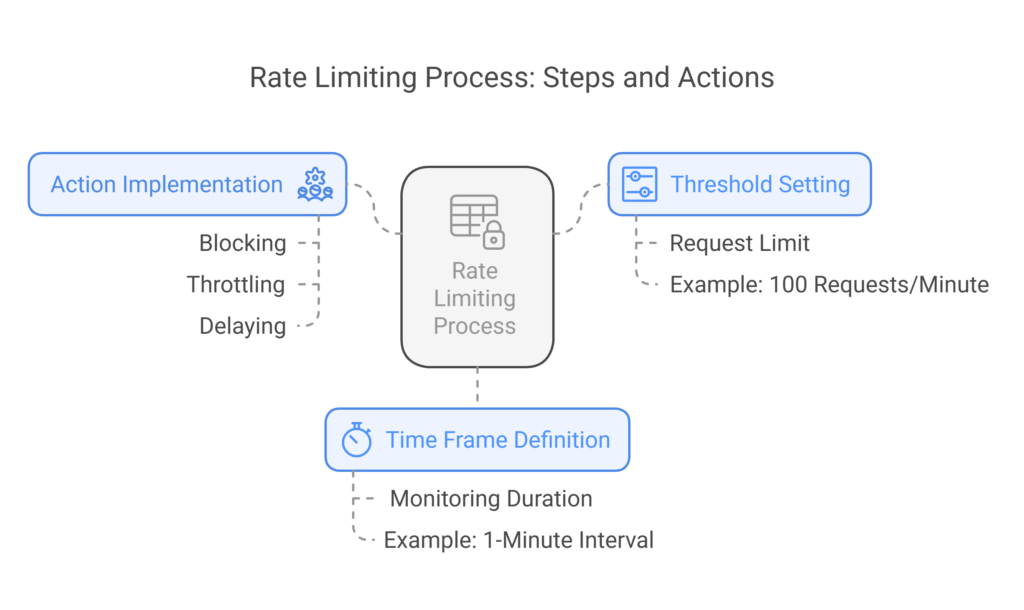
How Rate Limiting Works
- Threshold Setting: Define a request limit (e.g., 100 requests per minute).
- Time Frame Definition: Establish the monitoring duration (e.g., 1-minute interval).
- Action Implementation: Enforce blocking, throttling, or delaying excessive requests.
Real-World Example: Twitter’s API Rate Limits
Twitter implements API rate limiting to prevent excessive requests, ensuring fair access and protecting against spam bots and automation abuse.
Combining DDoS Protection and Rate Limiting
How These Measures Work Together
- DDoS Protection: Defends against large-scale traffic floods.
- Rate Limiting: Manages legitimate user requests and prevents misuse. By implementing both strategies, organizations can strengthen their cybersecurity posture, ensuring continuous availability and secure digital experiences.
Conclusion
Why These Measures Are Essential
- DDoS Protection safeguards businesses from downtime and service disruptions.
- Rate Limiting prevents abusive behavior and ensures resource fairness.
Final Thoughts
Adopting DDoS mitigation strategies and rate-limiting policies is crucial for maintaining the integrity, performance, and security of online services. By integrating these measures, organizations can enhance their cybersecurity resilience against evolving threats.

DSA, High & Low Level System Designs
- 85+ Live Classes & Recordings
- 24*7 Live Doubt Support
- 400+ DSA Practice Questions
- Comprehensive Notes
- HackerRank Tests & Quizzes
- Topic-wise Quizzes
- Case Studies
- Access to Global Peer Community
Buy for 52% OFF
₹25,000.00 ₹11,999.00
Accelerate your Path to a Product based Career
Boost your career or get hired at top product-based companies by joining our expertly crafted courses. Gain practical skills and real-world knowledge to help you succeed.

Data Analytics
- 20+ Live Classes & Recordings
- 24*7 Live Doubt Support
- 15+ Hands-on Live Projects
- Comprehensive Notes
- Real-world Tools & Technologies
- Access to Global Peer Community
- Interview Prep Material
- Placement Assistance
Buy for 70% OFF
₹9,999.00 ₹2,999.00

SDE 360: Master DSA, System Design, AI & Behavioural
- 100+ Live Classes & Recordings
- 24*7 Live Doubt Support
- 400+ DSA Practice Questions
- Comprehensive Notes
- HackerRank Tests & Quizzes
- Topic-wise Quizzes
- Case Studies
- Access to Global Peer Community
Buy for 50% OFF
₹39,999.00 ₹19,999.00

Fast-Track to Full Spectrum Software Engineering
- 120+ Live Classes & Recordings
- 24*7 Live Doubt Support
- 400+ DSA Practice Questions
- Comprehensive Notes
- HackerRank Tests & Quizzes
- 12+ live Projects & Deployments
- Case Studies
- Access to Global Peer Community
Buy for 51% OFF
₹35,000.00 ₹16,999.00

DSA, High & Low Level System Designs
- 85+ Live Classes & Recordings
- 24*7 Live Doubt Support
- 400+ DSA Practice Questions
- Comprehensive Notes
- HackerRank Tests & Quizzes
- Topic-wise Quizzes
- Case Studies
- Access to Global Peer Community
Buy for 52% OFF
₹25,000.00 ₹11,999.00

Mastering Mern Stack (WEB DEVELOPMENT)
- 65+ Live Classes & Recordings
- 24*7 Live Doubt Support
- 12+ Hands-on Live Projects & Deployments
- Comprehensive Notes & Quizzes
- Real-world Tools & Technologies
- Access to Global Peer Community
- Interview Prep Material
- Placement Assistance
Buy for 53% OFF
₹15,000.00 ₹6,999.00

Mastering Data Structures & Algorithms
- 65+ Live Classes & Recordings
- 24*7 Live Doubt Support
- 400+ DSA Practice Questions
- Comprehensive Notes
- HackerRank Tests
- Access to Global Peer Community
- Topic-wise Quizzes
- Interview Prep Material
Buy for 40% OFF
₹9,999.00 ₹5,999.00
Reach Out Now
If you have any queries, please fill out this form. We will surely reach out to you.
Contact Email
Reach us at the following email address.
arun@getsdeready.com
Phone Number
You can reach us by phone as well.
+91-97737 28034
Our Location
Rohini, Sector-3, Delhi-110085