Encryption: AES, RSA, and TLS - A Complete Guide
Introduction to Encryption
Encryption is a cybersecurity technique that converts plaintext into unreadable ciphertext to protect sensitive data from unauthorized access. It plays a crucial role in securing online communications, financial transactions, and personal information.
Why is Encryption Important?
- Prevents Data Breaches: Protects sensitive data from hackers and cyber threats.
- Ensures Privacy: Keeps personal and financial information confidential.
- Secures Digital Communication: Used in messaging apps, online banking, and cloud storage.
- Compliance with Regulations: Meets industry standards like GDPR, HIPAA, and PCI DSS.

What is Encryption?
Encryption is a method of securing data by transforming readable text into coded information using encryption algorithms and keys. Only authorized users with the correct key can decrypt and access the original data.
Key Encryption Terms
- Plaintext: The original readable data before encryption.
- Ciphertext: The scrambled, unreadable data after encryption.
- Encryption Key: A secret code used for encrypting and decrypting data.
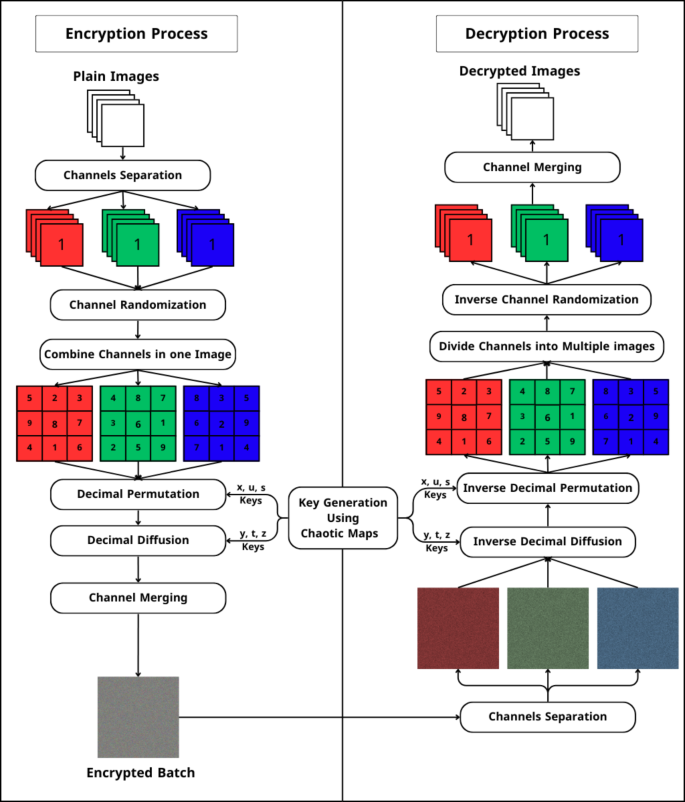
Types of Encryption: AES, RSA, and TLS
Encryption can be classified into symmetric and asymmetric encryption methods. Let’s explore the most widely used encryption algorithms:
AES (Advanced Encryption Standard)
- What It Is: A symmetric encryption algorithm where the same key is used for both encryption and decryption.
- Use Cases: Securing files, databases, and sensitive communications.
- Key Features:
- Highly efficient for encrypting large amounts of data.
- Commonly used in cloud storage and financial transactions.
RSA (Rivest-Shamir-Adleman)
- What It Is: An asymmetric encryption algorithm using a pair of keys (public and private) for encryption and decryption.
- Use Cases: Secure email communication, digital signatures, and SSL/TLS certificates.
- Key Features:
- Ensures secure key exchange.
- Used in secure login systems and authentication processes.
TLS (Transport Layer Security)
- What It Is: A security protocol that combines both symmetric and asymmetric encryption to protect data transmitted over the internet.
- Use Cases: Securing web traffic, online banking, and e-commerce transactions.
- Key Features:
- Ensures data integrity and authentication.
- Used in HTTPS to protect websites from cyber threats.
How Encryption Secures Online Banking Transactions
Encryption plays a vital role in securing financial transactions. Here’s how it protects your online banking activities:
Step 1: TLS Handshake
- Your browser and the bank’s server establish a secure connection using TLS.
- The server sends a public key, and your browser uses it to encrypt initial data.
Step 2: Data Encryption
- Your login credentials and financial data are encrypted using AES before transmission.
- The bank’s server decrypts the data using the shared key.
Step 3: Secure Transactions
- All online transactions are encrypted to prevent hackers from intercepting sensitive information.

Step-by-Step Guide: How Encryption Works
To implement encryption effectively, follow these steps:
Step 1: Choose the Right Encryption Algorithm
- Use AES for fast, symmetric encryption.
- Use RSA for secure key exchange.
Step 2: Generate Encryption Keys
- Symmetric Encryption: Create a single secret key.
- Asymmetric Encryption: Generate a public-private key pair.
Step 3: Encrypt the Data
- Convert plaintext into ciphertext using the chosen algorithm and key.
Step 4: Secure Data Transmission
- Use TLS encryption to ensure secure data transfer over networks.
Step 5: Decrypt the Data
- Authorized users use the correct decryption key to convert ciphertext back to plaintext.

Best Practices for Using Encryption
To maximize data security, follow these encryption best practices:
- Use Strong Algorithms: Implement AES-256 and RSA-2048 for high security.
- Protect Encryption Keys: Store keys securely and rotate them periodically.
- Enable HTTPS: Use TLS encryption for all websites and online transactions.
- Encrypt Data at Rest and in Transit: Protect stored and transmitted information.
Conclusion
Encryption is a fundamental component of cybersecurity, safeguarding data from unauthorized access. By understanding AES, RSA, and TLS, you can take proactive steps to secure your personal and business information. Whether you’re encrypting financial transactions, securing web communications, or protecting sensitive files, encryption ensures data privacy and security in the digital world.
Accelerate your Path to a Product based Career
Boost your career or get hired at top product-based companies by joining our expertly crafted courses. Gain practical skills and real-world knowledge to help you succeed.
Reach Out Now
If you have any queries, please fill out this form. We will surely reach out to you.
Contact Email
Reach us at the following email address.
arun@getsdeready.com
Phone Number
You can reach us by phone as well.
+91-97737 28034
Our Location
Rohini, Sector-3, Delhi-110085