Data Structures and Algorithms
- Introduction to Data Structures and Algorithms
- Time and Space Complexity Analysis
- Big-O, Big-Theta, and Big-Omega Notations
- Recursion and Backtracking
- Divide and Conquer Algorithm
- Dynamic Programming: Memoization vs. Tabulation
- Greedy Algorithms and Their Use Cases
- Understanding Arrays: Types and Operations
- Linear Search vs. Binary Search
- Sorting Algorithms: Bubble, Insertion, Selection, and Merge Sort
- QuickSort: Explanation and Implementation
- Heap Sort and Its Applications
- Counting Sort, Radix Sort, and Bucket Sort
- Hashing Techniques: Hash Tables and Collisions
- Open Addressing vs. Separate Chaining in Hashing
- DSA Questions for Beginners
- Advanced DSA Questions for Competitive Programming
- Top 10 DSA Questions to Crack Your Next Coding Test
- Top 50 DSA Questions Every Programmer Should Practice
- Top Atlassian DSA Interview Questions
- Top Amazon DSA Interview Questions
- Top Microsoft DSA Interview Questions
- Top Meta (Facebook) DSA Interview Questions
- Netflix DSA Interview Questions and Preparation Guide
- Top 20 DSA Interview Questions You Need to Know
- Top Uber DSA Interview Questions and Solutions
- Google DSA Interview Questions and How to Prepare
- Airbnb DSA Interview Questions and How to Solve Them
- Mobile App DSA Interview Questions and Solutions
DSA Interview Questions
- DSA Questions for Beginners
- Advanced DSA Questions for Competitive Programming
- Top 10 DSA Questions to Crack Your Next Coding Test
- Top 50 DSA Questions Every Programmer Should Practice
- Top Atlassian DSA Interview Questions
- Top Amazon DSA Interview Questions
- Top Microsoft DSA Interview Questions
- Top Meta (Facebook) DSA Interview Questions
- Netflix DSA Interview Questions and Preparation Guide
- Top 20 DSA Interview Questions You Need to Know
- Top Uber DSA Interview Questions and Solutions
- Google DSA Interview Questions and How to Prepare
- Airbnb DSA Interview Questions and How to Solve Them
- Mobile App DSA Interview Questions and Solutions
Data Structures and Algorithms
- Introduction to Data Structures and Algorithms
- Time and Space Complexity Analysis
- Big-O, Big-Theta, and Big-Omega Notations
- Recursion and Backtracking
- Divide and Conquer Algorithm
- Dynamic Programming: Memoization vs. Tabulation
- Greedy Algorithms and Their Use Cases
- Understanding Arrays: Types and Operations
- Linear Search vs. Binary Search
- Sorting Algorithms: Bubble, Insertion, Selection, and Merge Sort
- QuickSort: Explanation and Implementation
- Heap Sort and Its Applications
- Counting Sort, Radix Sort, and Bucket Sort
- Hashing Techniques: Hash Tables and Collisions
- Open Addressing vs. Separate Chaining in Hashing
- DSA Questions for Beginners
- Advanced DSA Questions for Competitive Programming
- Top 10 DSA Questions to Crack Your Next Coding Test
- Top 50 DSA Questions Every Programmer Should Practice
- Top Atlassian DSA Interview Questions
- Top Amazon DSA Interview Questions
- Top Microsoft DSA Interview Questions
- Top Meta (Facebook) DSA Interview Questions
- Netflix DSA Interview Questions and Preparation Guide
- Top 20 DSA Interview Questions You Need to Know
- Top Uber DSA Interview Questions and Solutions
- Google DSA Interview Questions and How to Prepare
- Airbnb DSA Interview Questions and How to Solve Them
- Mobile App DSA Interview Questions and Solutions
DSA Interview Questions
- DSA Questions for Beginners
- Advanced DSA Questions for Competitive Programming
- Top 10 DSA Questions to Crack Your Next Coding Test
- Top 50 DSA Questions Every Programmer Should Practice
- Top Atlassian DSA Interview Questions
- Top Amazon DSA Interview Questions
- Top Microsoft DSA Interview Questions
- Top Meta (Facebook) DSA Interview Questions
- Netflix DSA Interview Questions and Preparation Guide
- Top 20 DSA Interview Questions You Need to Know
- Top Uber DSA Interview Questions and Solutions
- Google DSA Interview Questions and How to Prepare
- Airbnb DSA Interview Questions and How to Solve Them
- Mobile App DSA Interview Questions and Solutions
Cybersecurity Interview Questions for Beginners and Experts
In today’s digital world, cybersecurity is a critical field, protecting systems, networks, and data from ever-evolving cyber threats. Whether you’re a beginner entering the cybersecurity industry or an expert aiming for a senior role, preparing for interviews is key to showcasing your skills. This comprehensive guide offers a curated list of cybersecurity interview questions for beginners, intermediates, and experts, complete with detailed answers to help you succeed in your next interview.
To boost your preparation, sign up for our free courses or get the latest updates on cybersecurity training by clicking here. These resources will enhance your knowledge and keep you ahead in this dynamic field.
Introduction
Cybersecurity involves safeguarding digital assets from threats like data breaches, malware, and phishing attacks. With cyberattacks occurring every 39 seconds on average, according to a 2024 study, the demand for skilled cybersecurity professionals is soaring. This guide addresses common interview questions across different experience levels, helping you demonstrate expertise and confidence. Whether you’re preparing for a junior role or a leadership position, these questions will provide valuable insights.
Beginner Level Questions
Beginners need a strong grasp of foundational concepts. Here are key questions often asked in entry-level cybersecurity interviews:
- What is cybersecurity?
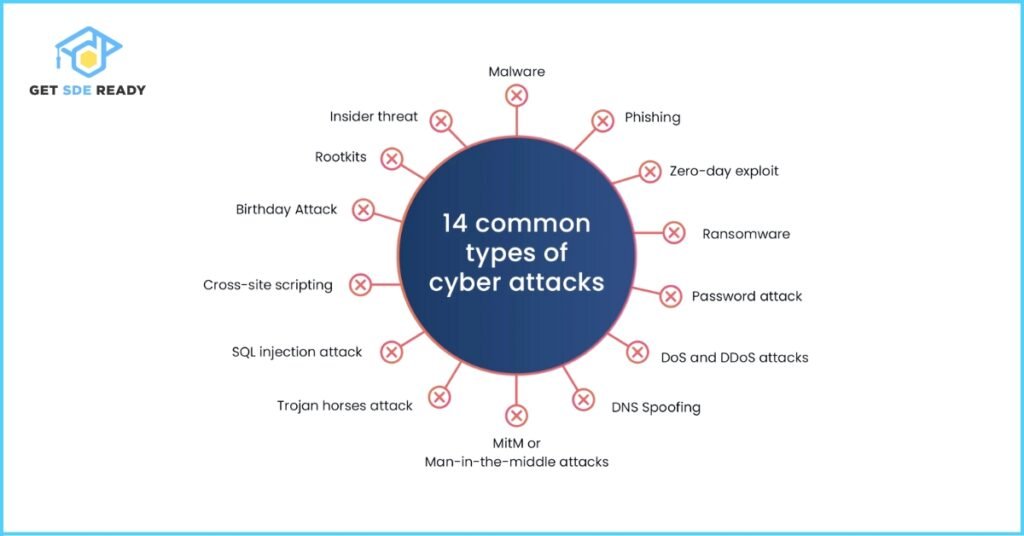
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks aimed at accessing, altering, or destroying sensitive information. It involves technologies, processes, and controls to ensure data confidentiality, integrity, and availability. - What are the types of cyberattacks?
Common cyberattacks include:- Malware: Malicious software like viruses or ransomware.
- Phishing: Deceptive emails or messages to steal sensitive data.
- Denial-of-Service (DoS): Overloading systems to disrupt availability.
- Man-in-the-Middle (MitM): Intercepting communications to steal data.
- SQL Injection: Exploiting database vulnerabilities to manipulate data.
3.What is a firewall and how does it work?
A firewall is a network security device that monitors and filters traffic based on predefined rules. It acts as a barrier between trusted and untrusted networks, blocking unauthorized access while allowing legitimate traffic.
4. What is encryption and why is it important?
Encryption converts readable data into an unreadable format (ciphertext) using algorithms and keys. It’s vital for protecting sensitive information, such as financial transactions or personal data, from unauthorized access.
5. What is two-factor authentication (2FA)?
2FA requires two forms of identification, such as a password (something you know) and a smartphone (something you have), to verify a user’s identity. It significantly enhances account security.
6. What is a honeypot?
A honeypot is a decoy system designed to attract and monitor cyber attackers. It mimics a real system but contains no sensitive data, helping organizations study attacker behavior.
7. What is social engineering?
Social engineering manipulates individuals into revealing confidential information or performing actions that compromise security, often through phishing or pretexting.
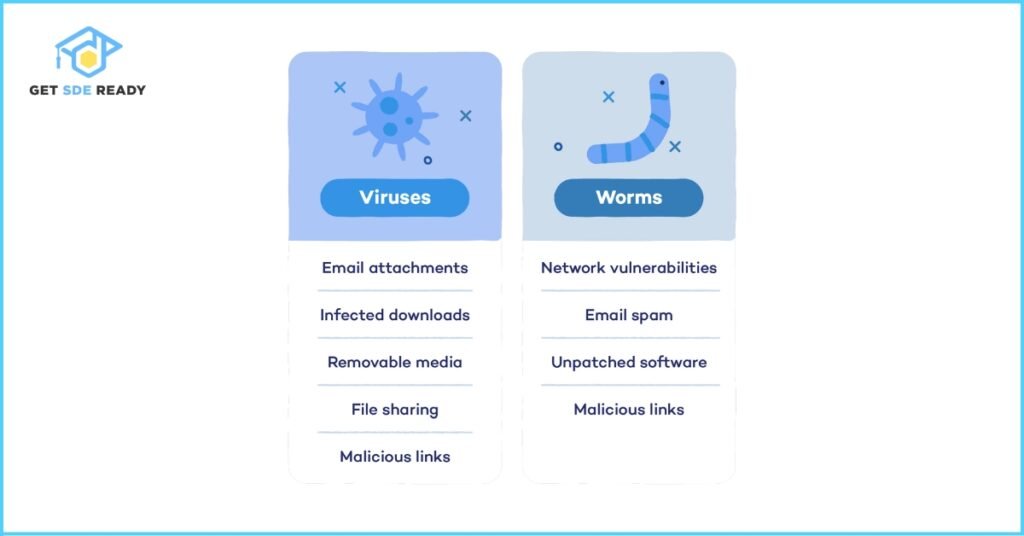
8. What is the difference between a virus and a worm?
- Virus: Malware that attaches to a host program and spreads when executed.
- Worm: Self-replicating malware that spreads across networks without user interaction.
9. What is a digital signature?
A digital signature uses cryptography to verify the authenticity and integrity of a message or document, ensuring it hasn’t been altered and comes from a trusted source.
10. What are common cybersecurity threats?
Threats include phishing, ransomware, DoS attacks, MitM attacks, SQL injections, and zero-day vulnerabilities, which exploit unknown software flaws.
Intermediate Level Questions
Intermediate questions test technical knowledge and practical application. These are often asked for roles requiring hands-on experience:
- What is penetration testing?
Penetration testing simulates cyberattacks to identify vulnerabilities in systems or networks. It uses ethical hacking techniques to assess security and recommend improvements. - What is a SIEM and how does it help in cybersecurity?
A Security Information and Event Management (SIEM) system collects and analyzes security data to detect and respond to threats in real time. It correlates logs and alerts to identify suspicious activity. - What are the key components of an incident response plan?
An effective plan includes:- Preparation: Training and policy development.
- Identification: Detecting and confirming incidents.
- Containment: Limiting damage and spread.
- Eradication: Removing the threat.
- Recovery: Restoring normal operations.
- Lessons Learned: Reviewing incidents for improvement.
- What is cloud security and what are its challenges?
Cloud security protects cloud-based data and applications. Challenges include data breaches, weak identity management, limited visibility, and shared responsibility between providers and users. - What is the difference between vulnerability assessment and penetration testing?
- Vulnerability Assessment: Identifies and quantifies system weaknesses.
- Penetration Testing: Actively exploits vulnerabilities to test defenses.
- What is a zero-day vulnerability?
A zero-day vulnerability is an unknown flaw in software or hardware that attackers exploit before a patch is available. It requires proactive monitoring to mitigate. - What is the role of a Security Operations Center (SOC)?
A SOC monitors and responds to cybersecurity threats using tools like SIEM and intrusion detection systems, ensuring rapid incident detection and response. - What is compliance in cybersecurity?
Compliance involves adhering to regulations like GDPR, HIPAA, or PCI DSS to protect data and maintain trust. It ensures organizations meet legal and industry standards. - What is public key infrastructure (PKI)?
PKI is a framework for managing digital certificates and encryption keys. It enables secure communication, authentication, and data integrity. - What is ethical hacking?
Ethical hacking involves authorized testing of systems to identify vulnerabilities, helping organizations strengthen security without malicious intent.
Expert Level Questions
Expert-level questions focus on advanced topics and strategic thinking, often for senior or specialized roles:
- What are advanced persistent threats (APTs)?
APTs are sophisticated, targeted attacks where intruders gain prolonged, undetected access to networks, often to steal sensitive data.
2. How does blockchain technology enhance cybersecurity?
Blockchain provides a decentralized, tamper-proof ledger for secure transactions, identity management, and data integrity, reducing single points of failure.
3. What are the challenges in securing IoT devices?
Challenges include:
- Heterogeneity: Diverse device types with varying security.
- Resource Constraints: Limited processing power for security measures.
- Scalability: Managing security for millions of devices.
Privacy: Protecting user data collected by IoT devices.
4. How can AI and machine learning be used in threat detection?
AI and machine learning analyze large datasets to detect anomalies, predict threats, and automate responses, improving the speed and accuracy of threat detection.
5.What is the role of threat intelligence in cybersecurity?
Threat intelligence provides insights into threat actors, tactics, and techniques, enabling proactive defense and informed decision-making.
6.What are the challenges in hybrid cloud security?
Challenges include maintaining consistent security policies, securing data across environments, ensuring visibility, and meeting compliance requirements.
7.What is quantum cryptography?
Quantum cryptography uses quantum mechanics to secure communication, offering theoretically unbreakable encryption based on physical laws.
8. How does DevOps impact cybersecurity?
DevOps emphasizes rapid development and deployment, requiring integrated security practices (DevSecOps) to ensure secure code and infrastructure.
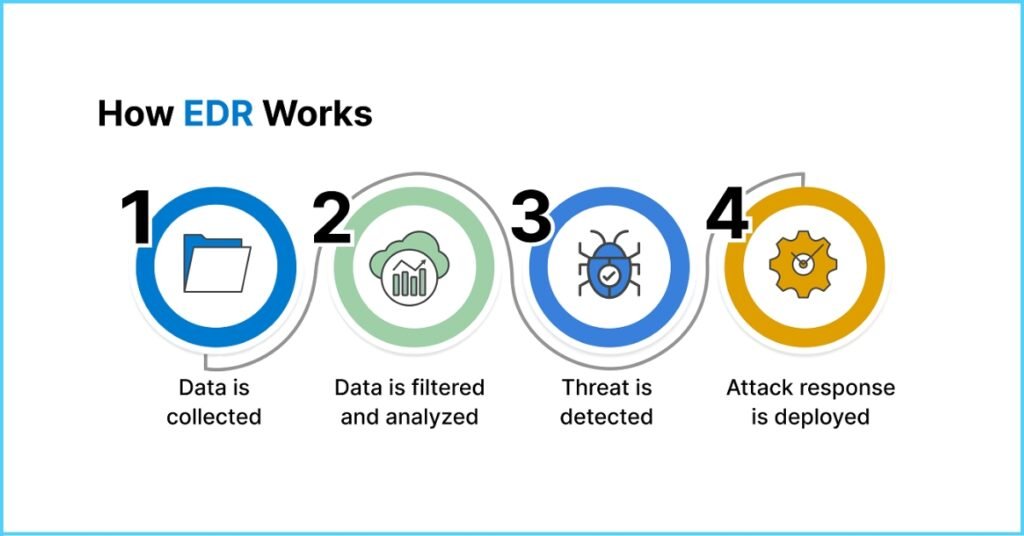
9. What is endpoint detection and response (EDR)?
EDR tools monitor and respond to threats on endpoints, providing real-time detection, investigation, and mitigation of suspicious activities.
10. What are the latest trends in cybersecurity?
Trends include increased use of AI for threat detection, zero-trust architecture, cloud-native security, and focus on securing remote work environments.
Conclusion
Mastering cybersecurity interview questions requires understanding both foundational and advanced concepts. This guide equips you with the knowledge to confidently tackle interviews at any level. Continuous learning is crucial in this fast-evolving field, so consider exploring resources like our Data Structures and Algorithms, Web Development, Master DSA, Web Dev, System Design, Data Science, and Crash Course to stay ahead.
FAQs
What are the most common cyber threats today?
Common threats include phishing, malware, ransomware, and DoS attacks, with 2,200 attacks occurring daily, per 2024 data.
How can I protect my personal information online?
Use strong passwords, enable 2FA, avoid suspicious links, and keep software updated to safeguard your data.
What is the difference between a virus and a worm?
A virus requires a host program to spread, while a worm self-replicates across networks without user interaction.
Why is cybersecurity important for businesses?
It protects sensitive data, ensures compliance, maintains customer trust, and prevents financial losses from cyberattacks.
What skills are essential for a cybersecurity professional?
Key skills include networking, programming, risk management, incident response, and problem-solving.

DSA, High & Low Level System Designs
- 85+ Live Classes & Recordings
- 24*7 Live Doubt Support
- 400+ DSA Practice Questions
- Comprehensive Notes
- HackerRank Tests & Quizzes
- Topic-wise Quizzes
- Case Studies
- Access to Global Peer Community
Buy for 52% OFF
₹25,000.00 ₹11,999.00
Accelerate your Path to a Product based Career
Boost your career or get hired at top product-based companies by joining our expertly crafted courses. Gain practical skills and real-world knowledge to help you succeed.

Data Analytics
- 20+ Live Classes & Recordings
- 24*7 Live Doubt Support
- 15+ Hands-on Live Projects
- Comprehensive Notes
- Real-world Tools & Technologies
- Access to Global Peer Community
- Interview Prep Material
- Placement Assistance
Buy for 70% OFF
₹9,999.00 ₹2,999.00

SDE 360: Master DSA, System Design, AI & Behavioural
- 100+ Live Classes & Recordings
- 24*7 Live Doubt Support
- 400+ DSA Practice Questions
- Comprehensive Notes
- HackerRank Tests & Quizzes
- Topic-wise Quizzes
- Case Studies
- Access to Global Peer Community
Buy for 50% OFF
₹39,999.00 ₹19,999.00

Fast-Track to Full Spectrum Software Engineering
- 120+ Live Classes & Recordings
- 24*7 Live Doubt Support
- 400+ DSA Practice Questions
- Comprehensive Notes
- HackerRank Tests & Quizzes
- 12+ live Projects & Deployments
- Case Studies
- Access to Global Peer Community
Buy for 51% OFF
₹35,000.00 ₹16,999.00

DSA, High & Low Level System Designs
- 85+ Live Classes & Recordings
- 24*7 Live Doubt Support
- 400+ DSA Practice Questions
- Comprehensive Notes
- HackerRank Tests & Quizzes
- Topic-wise Quizzes
- Case Studies
- Access to Global Peer Community
Buy for 52% OFF
₹25,000.00 ₹11,999.00

Mastering Mern Stack (WEB DEVELOPMENT)
- 65+ Live Classes & Recordings
- 24*7 Live Doubt Support
- 12+ Hands-on Live Projects & Deployments
- Comprehensive Notes & Quizzes
- Real-world Tools & Technologies
- Access to Global Peer Community
- Interview Prep Material
- Placement Assistance
Buy for 53% OFF
₹15,000.00 ₹6,999.00

Mastering Data Structures & Algorithms
- 65+ Live Classes & Recordings
- 24*7 Live Doubt Support
- 400+ DSA Practice Questions
- Comprehensive Notes
- HackerRank Tests
- Access to Global Peer Community
- Topic-wise Quizzes
- Interview Prep Material
Buy for 40% OFF
₹9,999.00 ₹5,999.00
Reach Out Now
If you have any queries, please fill out this form. We will surely reach out to you.
Contact Email
Reach us at the following email address.
arun@getsdeready.com
Phone Number
You can reach us by phone as well.
+91-97737 28034
Our Location
Rohini, Sector-3, Delhi-110085